To totally unlock this section you need to Log-in
Login
A smurf attack is an exploitation of the Internet Protocol (IP) broadcast addressing to create a denial of service.
Threat Symptoms and Risks
It's possible to accidentally download the Smurf Trojan from an unverified website or via an infected or fake email link.
Typically, the malware program will remain dormant on a computer until activated by a remote user (attacker); as a result, many Smurfs come bundled with rootkits, allowing hackers to create backdoors for easy system access. One way to combat a Smurf attack is to turn off IP broadcast addressing on every network router.
This function is rarely used, and if turned off it is not possible for the attack to overwhelm a network.
If a Smurf DDoS attack does succeed, it can cripple company servers for hours or days, resulting in lost revenue and customer frustration — what's more, this kind of attack may also be a cover-up for something more sinister, such as theft of files or other intellectual property (IP).
Dealing with Smurf and similar DDoS attacks requires a robust prevention strategy that is able to monitor network traffic and detect any oddities, for example packet volume, behavior and signature; many malware bots exhibit specific characteristics, and the right security service can help shut down a Smurf or other DDoS attack before it begins.
What it does?
A smurf attack is a type of denial of service attack in which a system is flooded with spoofed ping messages. This creates high computer network traffic on the victim’s network, which often renders it unresponsive.
Smurfing takes certain well-known facts about Internet Protocol and Internet Control Message Protocol (ICMP) into account. ICMP is used by network administrators to exchange information about network state, and can also be used to ping other nodes to determine their operational status.
The smurf program sends a spoofed network packet that contains an ICMP ping. The resulting echo responses to the ping message are directed toward the victim’s IP address. Large number of pings and the resulting echoes can make the network unusable for real traffic.
The attack in-depth
The following steps lead to a smurf attack:
- Huge numbers of ICMP requests are sent to the victim's IP address
- The source destination IP address is spoofed
- The hosts on the victim's network respond to the ICMP requests
This creates a significant amount of traffic on the victim’s network, resulting in consumption of bandwidth and ultimately causing the victim’s server to crash.
The smurf program builds a network packet that appears to originate from another address (this is known as spoofing an IP address). The packet contains an ICMP ping message that is addressed to an IP broadcast address, meaning all IP addresses in a given network. The echo responses to the ping message are sent back to the "victim" address. Enough pings and resultant echoes can flood the network making it unusable for real traffic.
To prevent a smurf attack, individual hosts and routers can be configured to be non-responsive to external ping requests or broadcasts. This is one of several suggestions provided by the CERT Coordination Center. Routers can also be configured to ensure that packets directed to broadcast addresses are not forwarded.
Thus, to prevent your network from being abused as an amplifier network in a SMURF attack, you should turn off the forwarding of directed broadcast on all router ports or take other measures to assure your network cannot be abused in this manner.
Another component which is important in this type of attack is that the attacker has to be able to inject packets into the network with forged IP source addresses. It is possible to enable functions in routers which will prevent the trivial forgery of IP source addresses, and doing so for a local network will prevent SMURF attacks from being launched locally. Do however note that access lists can have a performance impact, so judicious use of such tools is advised.
This sort of ingress filtering has been documented in RFC2267, and is effective not only for preventing local origination of SMURF attacks, and also makes tracking attacks (or denying origination of attacks) much easier.
Since SMURF attacks use forged source addresses, tracking SMURF attacks back to their source can be a challenge. It has to be done while the attack is ongoing, and requires the swift cooperation of all the network service providers along the path.
The power of ICMP
You might be asking, “How could a little ping traffic take down a site?”.
Well, suppose the hacker has a cable modem or a T-1 connection and sends a 1-Mbps spoofed ICMP stream at the intermediary sites. Now suppose the intermediary sites have 150 hosts that respond. This yields a 150-Mbps attack traveling from the “amplifiers” toward the victim. The cracker (black-hat hacker) can keep this up as long as he has a connection and as long as the amplifiers continue to broadcast the ICMP traffic.
What is a SMURF aplifier
A Smurf amplifier is a computer network that lends itself to being used in a Smurf attack. Smurf amplifiers act to worsen the severity of a Smurf attack because they are configured in such a way that they generate a large number of ICMP replies to the victim at the spoofed source IP address.
Don’t be a part of the problem
First, don’t let someone on your network perpetrate this type of attack on someone else. In order for the attack to start, the first network had to let a source-spoofed IP packet leave its network.
You can stop this kind of attack from leaving your network by applying an outbound filter to your perimeter router. An example of how to accomplish this with a Cisco router would be:
Access-list 100 permit IP {your network address} {your network mask} any
Access-list 100 deny IP any any
Apply this access list to your network’s outbound connection on your perimeter router. This stops anybody on your network from sending source-spoofed packets outside the local network.
Second, stop your network from being used as an amplifier. Unless you absolutely need broadcast capability outside your network, use the "no ip directed-broadcast" command on every interface on your router.
Alternatively, if you’re running a larger, more robust network with multiple routers, use the ip verify unicast reverse-path command on your perimeter router, and the router will verify that it has a reverse path for the spoofed ICMP packet and drop the packet if no path exists. You must have Cisco Express Forwarding (CEF), or something similar from another vendor, running because the lookup uses the Forwarding Information Base (FIB) that CEF creates.
Properly configured network equipment is the key
The availability of the directed broadcast function is an important element in these attacks. The current Proposed Standard for "Requirements for IP Version 4 Routers" (RFC1812) states that a router must default to forwarding directed broadcasts, that a knob must exist to turn it off, but it must default to the «on» position (see section 5.3.5.2 of RFC1812).
However, the current sentiment is that this should no longer be a requirement.
How to track
To track down the true source of this type of attack, you should take the following steps:
- Determine the amplifiers’ IP space and contact their network administrator. Remember that the packets you are seeing are coming from the amplifier, not the hacker.
- Ask them to log inbound traffic from your victim IP address. These will be the source-spoofed packets.
- Get the MAC address of the source-spoofed packets and have them do a show ip arp (if using Cisco IOS) on that MAC address.
- The results will yield the hop from which the source-spoofed packets came.
- Find who controls the router from that hop and contact their network administrator.
- Repeat steps 2-5 until you find a router that has a direct link to the MAC address you’re tracking.
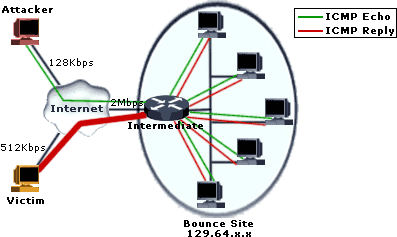
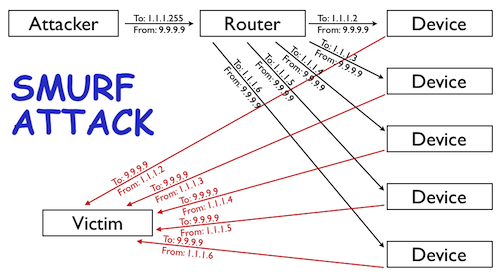


In a world connected through billions of devices, SMURF or generic DDoS attacks could be devastating on businesses and organizations, hospitals or other infrastructures and could have abnorm impacts on communications. To prevent this dangerous type of attack network administrators have to know very well how this attack can be mitigated and prevented.
Read more on HeelpBook.net:
What is a smurf attack? – http://heelpbook.altervista.org/2014/what-is-a-smurf-attack/ #network #security #glossary #botnet #heelpbook – http://www.heelpbook.net @heelpbook