To totally unlock this section you need to Log-in
Login
Many of today’s Enterprise datacenters are running some form of virtualization. Server virtualization allows us to clone VMs. When it comes to Server 2012, the cloned VM with Server 2012 has duplicate copy of SID of machine from which it was cloned.
The duplicate SID value causes lot of issues so each machine must have unique SID value. In this post, we will show steps to generate new SID in Server 2012 R2.
Generate New SID (Windows Server 2012)
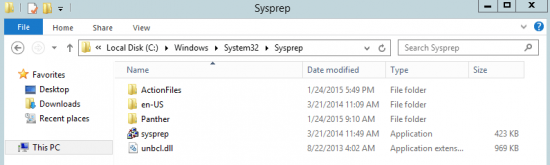
Log on to Windows Server. Open Windows Explorer, and browse, C:\Windows\System32\Sysprep:
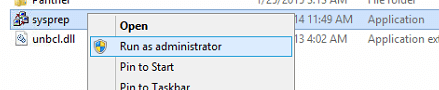
Right-click sysprep application and click Run as Administrator.
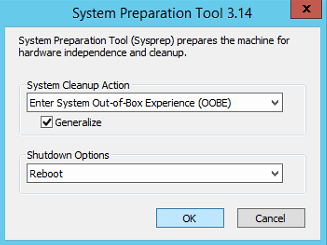
System Preparation tool will open as shown below. Choose Enter System Out-of-Box Experience (OOBE) option, check Generalize option, choose Reboot as shutdown options and click OK.
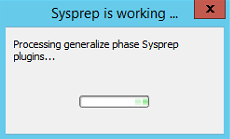
The application will generate new SID and perform all the required actions and will reboot.
After the reboot, you will be asked to enter the product key (optional), accept License terms, and enter new Administrator password. You can then, login to the server and change Host name and IP address. In this way you can generate new SID.
Checking SID
The computer SID is stored in the HKEY_LOCAL_MACHINE\SECURITY\SAM\Domains\Account registry subkey. This key has a value named F and a value named V. The V value is a binary value that has the computer SID embedded within it at the end of its data. This SID is in a standard format (three 32-bit subauthorities preceded by three 32-bit authority fields).
Because you can't see the SECURITY hive's contents by default (even as an administrator), you need a little trick. Use at command to schedule the startup of PowerShell. Make sure that you schedule the task as Interactive and that the Scheduler service runs in the security context of the System (aka LocalSystem) account because this account, unlike a regular user account, has privileges to view the SAM and SECURITY hives.
C:\> at TIME /interactive powershell.exe
PS> $key = Get-Item HKLM:\security\sam\domains\account PS> $values = Get-ItemProperty $key.pspath PS> $bytearray = $values.V PS> New-Object System.Security.Principal.SecurityIdentifier($bytearray[272..295],0) | Format-List *
BinaryLength : 24 AccountDomainSid : S-1-5-21-796845957-602608370-839522115 Value : S-1-5-21-796845957-602608370-839522115
You can check your result with Sysinternals PsGetSid tool:
PS> .\psgetsid.exe
SID for \\COMPUTER: S-1-5-21-796845957-602608370-839522115