To totally unlock this section you need to Log-in
Login
In a domain environment, that could be a common issue about certificates auto-enrollment, with common events error like 6 and 13. Let's see how to fix them.
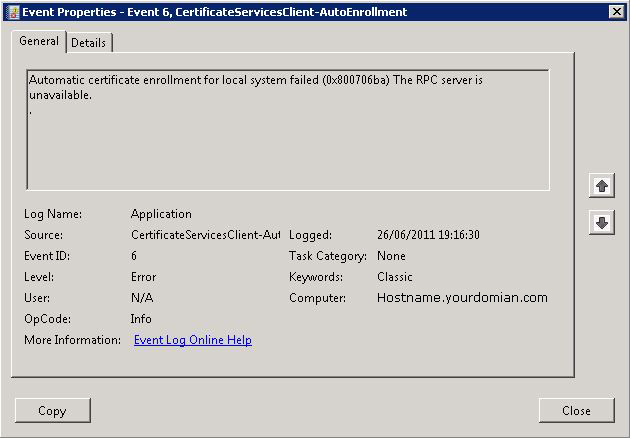
Event ID 6
Source: Microsoft-Windows-CertificateServicesClient-AutoEnrollment
Description: Automatic certificate enrollment for local system failed (0x800706ba) The RPC server is unavailable.
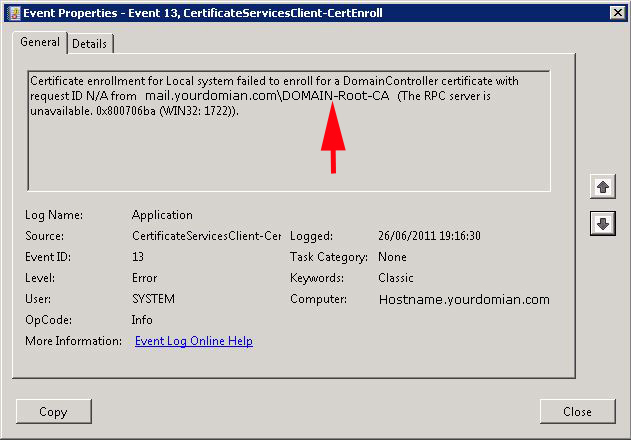
Event ID 13
Source: Microsoft-Windows-CertificateServicesClient-CertEnroll
Description: Certificate enrollment for Local system failed to enroll for a DomainController certificate with request ID N/A from {hostname}{name of CA}(The RPC server is unavailable. 0x800706ba (WIN32: 1722)).
Solution
Note: The pertinent information in the Event ID 13 above is 0x800706ba there are Other causes of this Event ID make sure yours is the same.
In a sample case we could have an Exchange server that was using a certificate that had been "self signed". And the Root CA that signed the certificate had been ungracefully removed from the domain. Take a note of the Root CA name from the Event ID error shown arrowed).
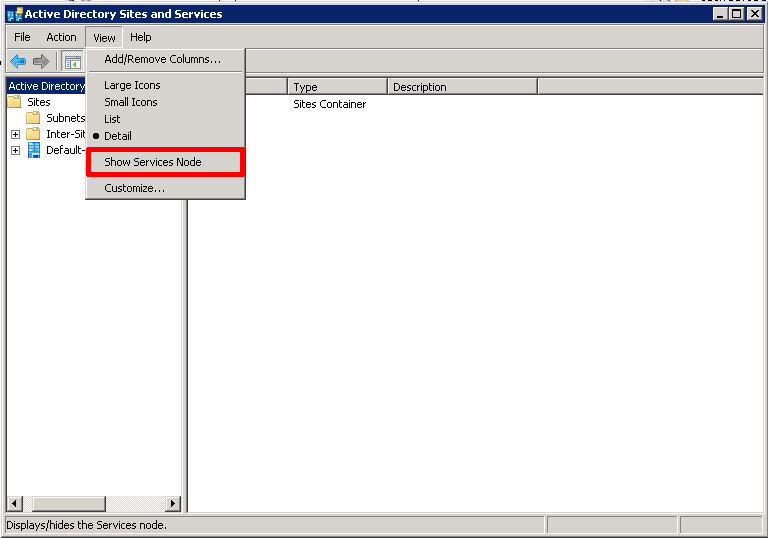
Launch Active Directory Sites and Services" > Select the top level object > View > Show Services Node.
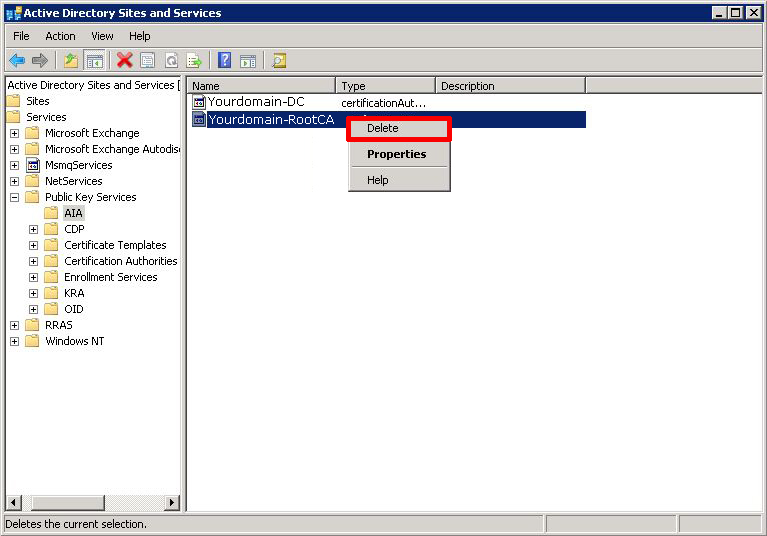
Expand Services > Public Key Services > AIA > Delete the "Problem CA".
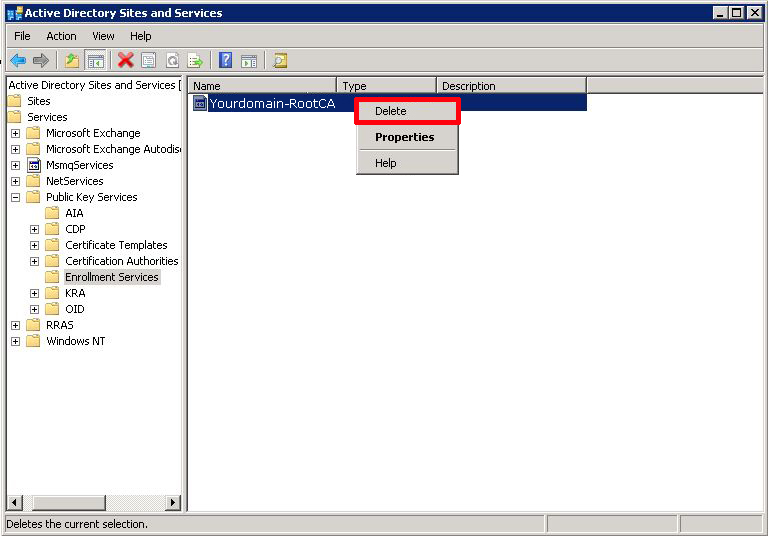
Then select "Enrollment Services" > Delete the "Problem CA".
IMPORTANT: If you have a New CA, then DO NOT perform the next two steps!!!
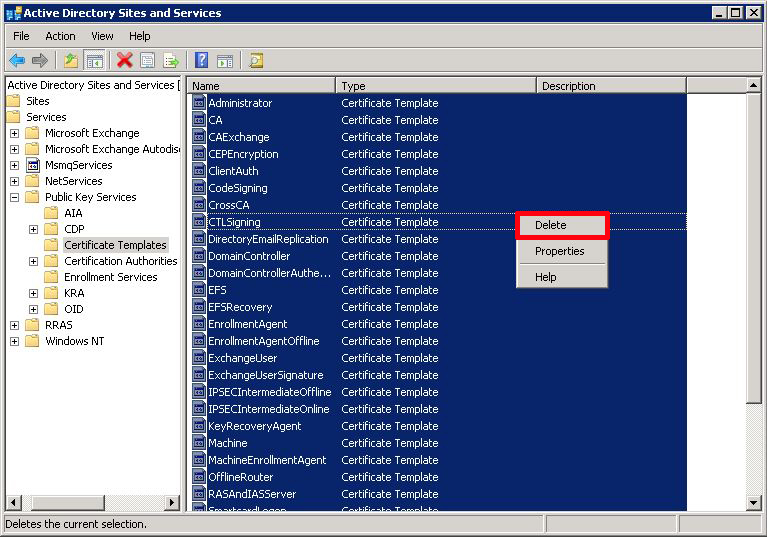
Providing you DON'T have a CA now, select "Certificate Templates" and delete them all.
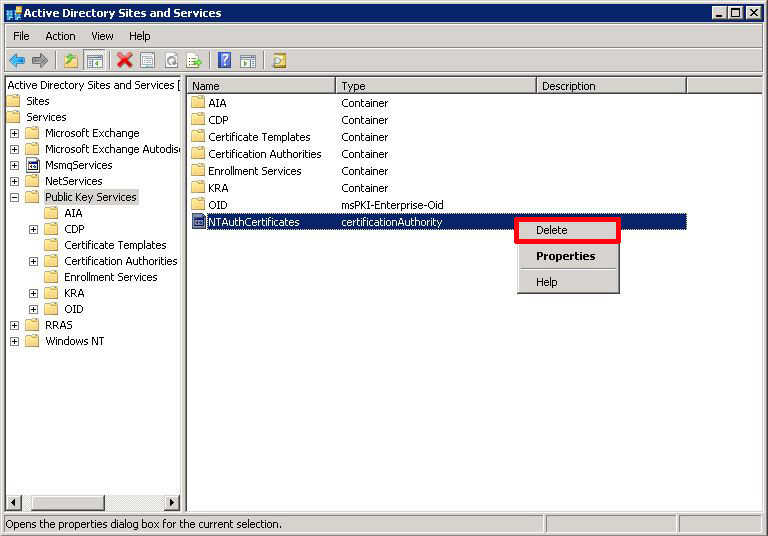
Providing you DON'T have a CA now, select "Public Key Services" and delete the NTAuthCertificates item.
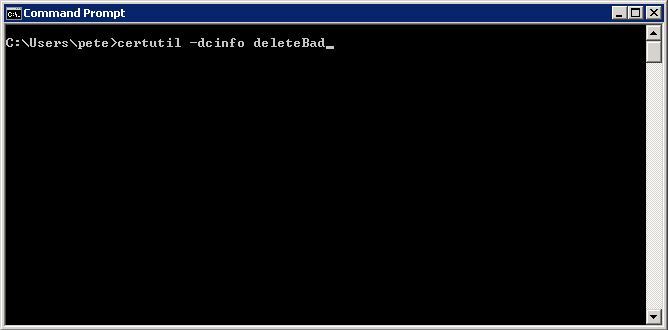
To tidy up, (on the server logging the error) run the following command:
certutil -dcinfo deleteBad
Finally on the server logging the error run the following command to update the policies:
gpupdate /force