To totally unlock this section you need to Log-in
Login
The Lightweight Directory Access Protocol is an application protocol for accessing and maintaining distributed directory information services over an Internet Protocol (IP) network.
Directory services may provide any organized set of records, often with a hierarchical structure, such as a corporate email directory. Similarly, a telephone directory is a list of subscribers with an address and a phone number.
Distinguished Names
If you want to access a directory object, a special LDAP-Name has to be used for each object - this applies for single objects as well as for whole containers. For example:
cn=Name Surname,ou=Consultants,ou=colleague,dc=example,dc=com
Actually, these are no special LDAP-Pathnames, but technical notations for X.500-Directory Objects. All directory services at least strive towards compatibility with the X.500 directory standard.
The notation for X.500-Directory objects is also called Distinguished Name (DN).
Originally, the syntax of Distinguished Names was established in RFC 1779 and RFC 2253. In the meantime, the more modern RFC-Specification RFC 4514 applies here.
A Distinguished Name represents an object in a hierarchical directory, at which the DN is written from lower to superior hierarchical levels from left to right. Every hierarchy level is written as follows:
keyword=object
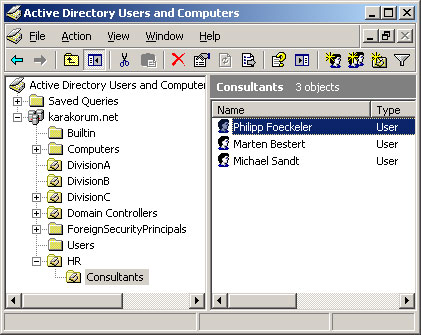
The Distinguished Name for the object 'Philipp Foeckeler' in the domain 'example.com' would look like this:
cn=Philipp Foeckeler,ou=Consultants,ou=HR,dc=example,dc=com
In this case, the notation for only the object (without the remaining LDAP-Path) would be the so-called Relative Distinguished Name (RDN):
cn=Philipp Foeckeler
The value of the Relative Distinguished Names (in this case 'Philipp Foeckeler') is exactly the notation with which the object in the Active Directory administration is visible, too. It has nothing to do with the displayname of an AD object and can only be changed with the function F2 (Context menu-> Rename).
The keywords (cn, ou, dc etc.) aren't case sensitive and have the following meanings:
cn: Common Name
ou: Organizational Unit
dc: Domain Component
These are the three keywords mainly used in Active Directory LDAP. However, any kind of keyword is possible. Accordingly, other directory systems often might use different keywords for their container objects:
l: Location
o: Organization
st: State/Province/Federal State
c: Country
The keyword 'organization' (O) is often used as top level of a non-AD directory system instead of DC keywords that always represent the top level in Active Directory environments.
Complete LDAP Paths
Quite often, not only the Distinguished Name (DN) of a directory object has to be provided but a complete LDAP pathname, i.e. a URL (Unified Resource Locator). Then two elements have to be added to the distinguished name: The label of the LDAP protocol and the server name to which you want to connect:
LDAP://server/distinguished-name
The server is the one to which the LDAP connection is set up. If the server name is left out, it's always the local PC it refers to. Some examples:
LDAP://cn=George Mallory,ou=Alpinist,dc=himalaya,dc=net
LDAP://everest.himalaya.net/cn=George Mallory,ou=Alpinist,dc=himalaya,dc=net
In this case, the NetBIOS name can be used too:
LDAP://EVEREST/cn=George Mallory,ou=Alpinist,dc=himalaya,dc=net
IP addresses are possible as well:
LDAP://192.168.57.3/cn=George Mallory,ou=Alpinist,dc=himalaya,dc=net
Typically, an LDAP connection is set up on TCP-Port 389. If the server offers its LDAP services under another port, then, like in other URLs, this can be stated together with the server name:
LDAP://everest.himalaya.net:390/cn=George Mallory,ou=Alpinist,dc=himalaya,dc=net
LDAP://EVEREST:390/cn=George Mallory,ou=Alpinist,dc=himalaya,dc=net
LDAP://192.168.57.3:390/cn=George Mallory,ou=Alpinist,dc=himalaya,dc=net
In doing so, e.g. the Global Catalog can be retrieved, which is provided by appropriately configured Active Directory domain controllers under TCP-Port 3268:
LDAP://everest:3268/dc=himalaya,dc=net
Especially for the LDAP connection to Active Directory domain controllers, an alternative LDAP path can be used:
GC://everest/dc=himalaya,dc=net
Special Characters in the Distinguished Name
Most of the modern LDAP servers can handle easily the special characters of the ASCII table (for example the german o-umlaut). However, a few restrictions apply when building a Distinguished Name:
1. If object names (RDN names) shall start or end a space character, this must be preceeded with a leading backslash '\'.
2. If the following characters shall be used in an object name, they also have to be escaped with leading backslash '\'.
, + " \ <> ; =
3. If object names shall start with a "#" this must be preceeded with a leading backslash '\'. Especially for AD domain controllers or ADAM servers it's a strange effect that the system uses the escaping backslash for the '#' at all position in the name string. Normally this is not neccessary, the backslash is only important at the beginning because modern LDAP servers accept a syntax where a name starts with "#" and consist then of a hex code for the name.
4. Additionally, any character can be expressed with it's UTF8 value, encoded with a leading backslash for each value. So in environements where the LDAP server doesn't acccept pure UTF-8 strings for distinguished names, you can easily encode all special characters for your object's names.
don't need this encoding in Active Directory environements, because you can use UTF-8 strings with special chars directly as distinguished names.
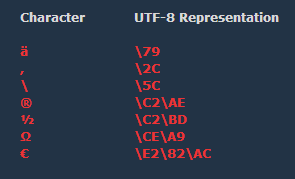
Here are some examples for UTF-8 escaped characters:
A few general examples for special characters in the distinguished name:
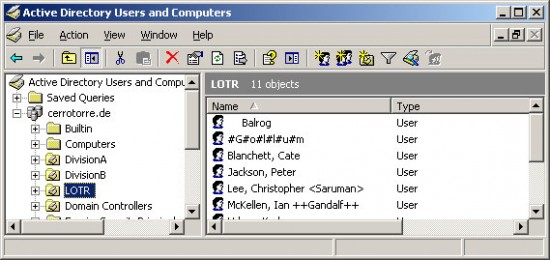
These objects have the following Distinguished Names:
cn=\ Balrog, ou=LOTR,dc=cerrotorre,dc=de
cn=\#G#o#l#u#m#,ou=LOTR,dc=cerrotorre,dc=de
cn=Blanchet\, Cate,ou=LOTR,dc=cerrotorre,dc=de
cn=Jackson\2C Peter,ou=LOTR,dc=cerrotorre,dc=de
cn=Lee\, Christopher \,ou=LOTR,dc=cerrotorre,dc=de
cn=McKellen\, Ian \+\+Gandalf\+\+,ou=LOTR,dc=cerrotorre,dc=de
Active Directory Domain Names in LDAP-Paths
Again for clarification: As domains still play an important role in the Microsoft directory and domain names of the Active Directory have to be conform with the DNS system, Microsoft uses a special method for representing DNS domain names on X.500-compliant LDAP pathnames.
Thereby, the single components of a domain name are split up into separate dc-parts.
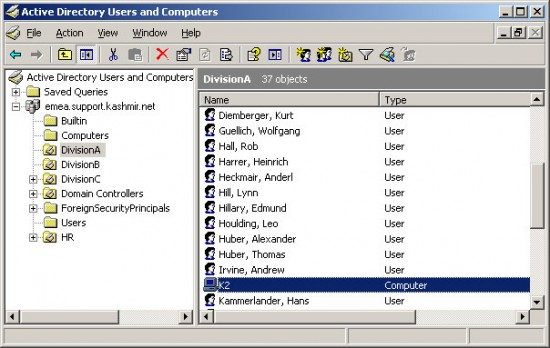
Thus, if you want to name an object of the domain emea.support.kashmir.net, the Distinguished Name will e.g. be:
cn=K2,ou=DivisionA,dc=emea,dc=support,dc=kashmir,dc=net
Active Directory Built-in Containers
Not all containers within an Active Directory domain are OU objects. Sometimes, they may represent CN objects. This applies particularly for the domain containers 'Users', 'Computers', and 'Builtin'.
Thus, it is not:
cn=Administrator,ou=Users,dc=company,dc=de (WRONG!!)
But:
cn=Administrator,cn=Users,dc=company,dc=de (RIGHT!!)
This difference can be recognized in the tool 'AD user and computer' at the container's icon:
Special Pathnames for eDirectory / NDS
In Novell eDirectory environments (formerly known as NDS: Novell Directory Services), LDAP pathnames are built by starting simply from the organization's name - the name of the eDirectory tree is not important.
Thus, the top level of the LDAP hierarchy is always the name of the organization (keyword 'o=') - after that just going through all organizational units up to the actual leaf object. For example:


Understanding LDAP Paths and Pathnames – http://heelpbook.altervista.org/2014/understanding-ldap-paths/ #howto #heelpbook #ldap #Microsoft @heelpbook